Cybersecurity Advisory for Linden Residents – Tax Collector Scams
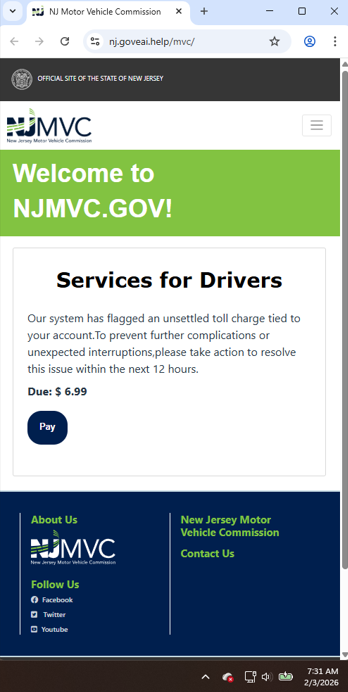
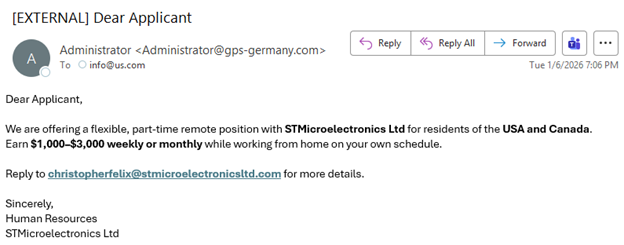
With tax season underway, we have observed a significant increase in tax-related phishing and vishing (voice phishing) campaigns over the past month. In these schemes, cybercriminals exploit legitimate cloud services to host malicious files designed to install sophisticated malware; specifically, a Remote Access Trojan (RAT). Once deployed, this malware grants threat actors persistent remote access to infected devices, enabling them to steal sensitive data and even deploy ransomware.
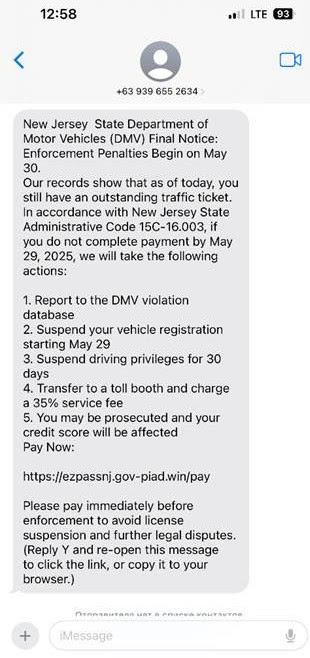
We have also received reports of fraudulent outbound phone calls in which scammers impersonate representatives from Tax Collector offices. To help protect Linden residents, it is important to understand exactly how our office operates.
How Our Office Communicates with You
Please be advised: the City of Linden’s Tax Collector’s office will never demand immediate payment over the phone. There are, however, specific circumstances where we may need to reach out to you directly. These calls generally occur when a property is in danger of having a lien placed due to non-payment, or when we encounter an issue with a recent payment, for example, if a check was returned due to account restrictions, if the payment amount was short, or if the check was filled out incorrectly.
In these instances, a legitimate representative from our office will always do the following:
- Clearly identify themselves by name.
- State that they are calling from the City of Linden Tax Collector’s office.
- Explain the specific issue with your account.
- Advise you to come into our office in person to resolve the matter. We will never demand an immediate payment method over the phone.
How to Protect Yourself
If you receive an unsolicited call from someone claiming to be from our office, hang up immediately. Do not engage, and do not provide any personal or financial information.
- If the call is legitimate: The caller will instruct you to visit our office. You can then verify the issue in person.
- If the call is a scam: The caller may attempt to pressure you for payment. Remember, we will never demand payment on the spot.
To verify the status of your account or report the call, always and only contact the City’s Tax Collector’s Department directly using the official phone numbers here.
It is also critical to note that threat actors are now recording victims’ voices during these calls. These recordings can be used to generate AI-powered voice clones to impersonate you in future scams. This is an emerging tactic that can be combatted by ending any suspicious call immediately without engaging the caller.
Always remember the following.
- Avoid clicking links, responding to, or acting on unsolicited text messages.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Report fraudulent activity to the Linden Police Department, to the NJCCIC, FTC, and FBI’s IC3, and forward the message to 7726 (SPAM).